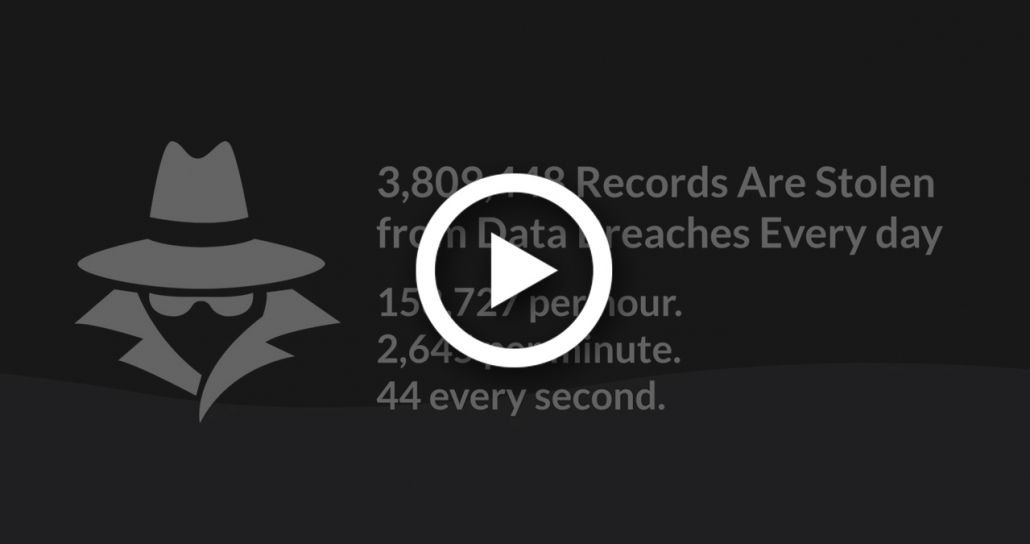
Why The Need For a Fresh Approach?
Data security has been on the same treadmill for decades –the treadmill of tightly integrating security into applications. Weekly stories of massive data and privacy breaches prove that the treadmill does not work.
The treadmill approach has led to every application implementing security its own way. The result is too complex for administrators and users. It costs too much and it’s not sustainable or manageable, not to mention ineffective.
About two decades ago, user identities were in a similar place as data security is today. Back then, every application managed its own identities and required its own user administration –the situation was unsustainable for users and administrators. What happened? Identity & Access Management (IAM) solutions came in and separated identities away from applications.
The world of information technology has changed a lot since then and it’s now time for a fresh approach to data security –one that’s easy to deploy and transparent to users. Cord3 separates data security from applications so your organization can have one data security policy that is implemented consistently across applications, not a different data security policy and approach for every application.